Steps for starting Safe Mode from a blank screen:
How to change UAC settings in Windows 7
Open the Windows Control Panel, and then click System and Security.
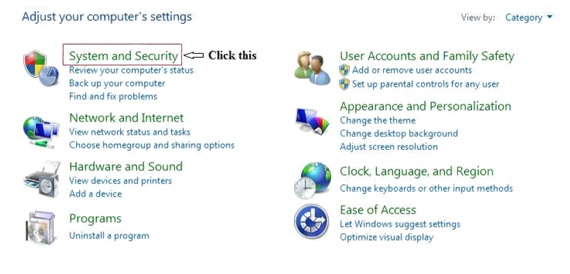
2. The System and Security window appears. Click Action Center
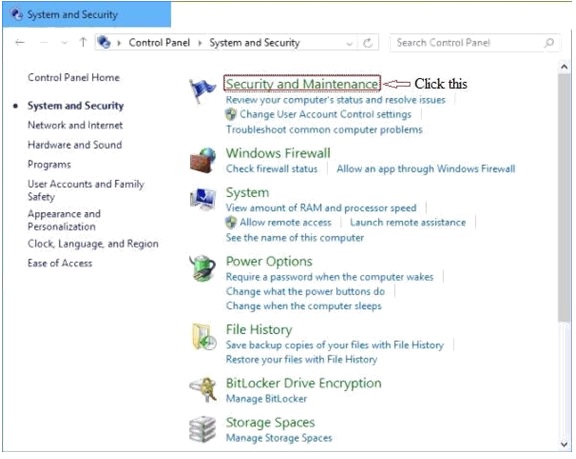
3. The Action Center window appears. In the left pane, click Change User Account Control
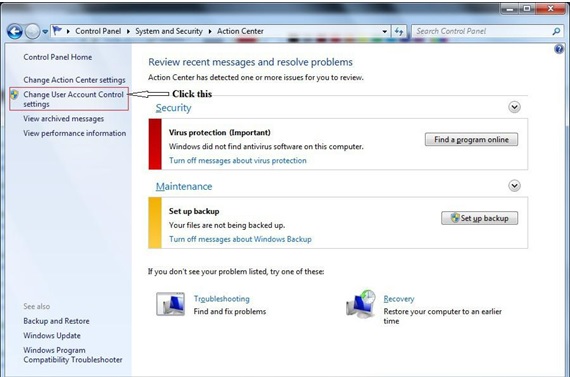
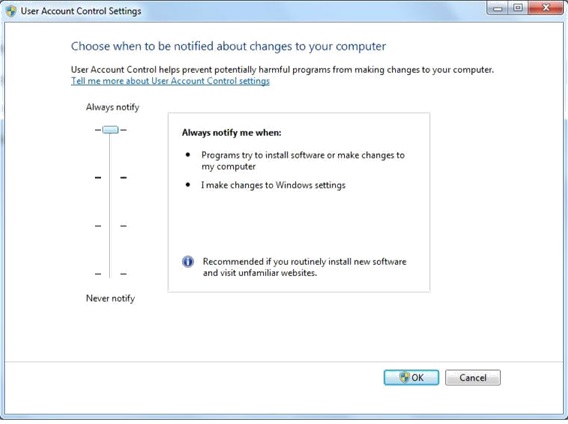
The User Account Control Settings dialog box appears, as shown in the figure below. Slide the vertical bar (on the left side) to your desired setting and click OK.
To change UAC settings in windows 10
1. In the control panel window click “System and Security”

2. To change UAC settings in windows 10.

3. To change UAC settings in windows 10.
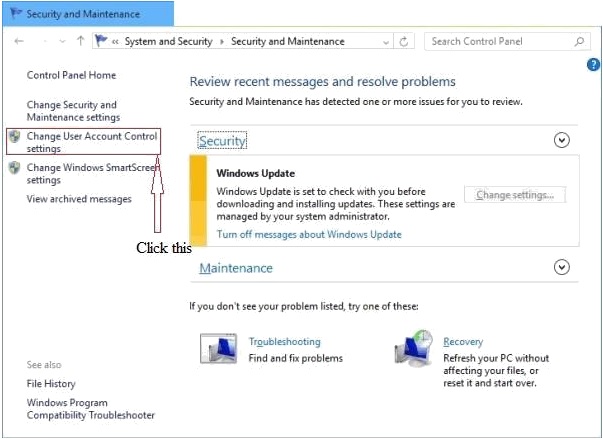
4. To change UAC settings in windows 10
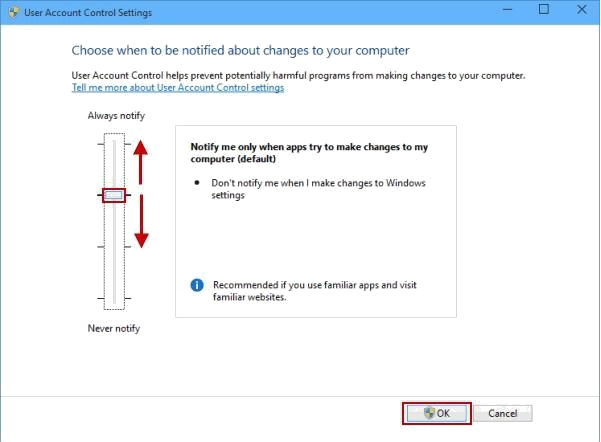
User Account Control notifies you when potentially harmful programs try to make changes to your PC, and you can choose when to be notified about changes to your computer through changing its settings.
1. By default, User Account Control will notify you only when apps try to make changes to your computer. And this setting is recommended if you use familiar apps and visit familiar websites, referring to the picture above.
2. If you move the scale to the top to select Always notify, you will be notified when apps try to install software or make changes to your PC and when you make changes to Windows settings. BTW, the setting is recommended if you routinely install new software and visit unfamiliar websites.
3. You can move the scale to choose the third option to ask User Account Control not to dim your desktop when notifying you about apps' up-coming changes to your computer if it takes a long time to dim the desktop.
4. Supposing that you don't want to be notified when apps try to install software and make changes to your PC and when you make changes to Windows settings, move the scale to the bottom to choose Never notify.
There are four possible UAC settings, described as follows:
Always notify: This is the most secure option. It notifies you anytime a program tries to make changes to your computer or to Windows settings. When you are notified of a pending change, your desktop is dimmed (to prevent other programs from running until a decision is made), and you must either approve or deny the change in the UAC dialog box.
Notify me only when programs try to make changes to my computer: This is the default setting Windows notifies you anytime a program tries to make changes to your computer or if a program outside of Windows attempts to make changes to a Windows setting.
Notify me only when programs try to make changes to my computer (do not dim my desktop): Same as the previous setting, except the desktop is not dimmed, which may allow some malicious programs to alter the appearance of the dialog box.
Never notify: This is the least secure setting. If you’re logged on as a standard user, changes that require administrator permissions will be denied. If you’re logged in as an administrator, those changes will be automatically permitted, potentially exposing your computer, network, and personal information to security risks.
Attempt to install legacy (older) applications in compatibility mode: Select the older OS that the application was originally written for. It is less likely that updates or the latest service pack(SP) will help in this situation. Security updates probably won't have an effect on this scenario either.
The problems such as video card, network card, and modem card can be resolved by booting to Safe Mode. While in Safe Mode, troubleshoot the problem. In Safe Mode, you can uninstall the driver(s) that is causing problem with normal boot process.
If your PC is slow, check for excessive paging. The most likely cause for excessive paging is due to insufficient Memory. Increase the physical Memory on your computer. Traditionally, workstations can have multiple operating systems installed on them but run only one at a time. By running virtualization software, the same workstation can be running Window 7 along with Windows Server 2008 and Red Hat Enterprise Linux (or almost any other operating system) at the same time, allowing a developer to test code in various environments as well as cut and paste between them within a virtual machine (VM).
If you are unable to remove a suspect file, boot in Safe Mode. In Safe Mode, only required services are loaded. It would typically be possible to remove the file in Safe Mode.
1. The spammer has hijacked your email address,
2. He spoofed your email address.
First step in resolving the problem is to change the account password. This wouldeliminate that some one hijacking your email account. In the second case, the attacker doesn't have access to your email account, but using your email ID as “From” address to send spam. The IP address, host name etc. would be different.
There is actually, no simple solution to this problem One feature that may be useful is DKIM. DKIM short for Domain Keys Identified Mail, is an email authentication method designed to detect email spoofing. It is a way to sign and verify email messages at the message transfer agent (MTA) level using public and private keys. The public keys are published in DNS TXT records. DKIM authenticates the source and its contents.
Email spam (Receiving email): Unsolicited mail is a big problem these days and there is no single solution to this problem. Sender Policy Framework (SPF) is an open standard specifying a technical method to prevent sender address forgery. SPF uses a DNS TXT record in the DNS zone file to limit the number of servers that are allowed to send email on behalf of a domain name. Basically, this tells the receivers, “messages for my domain should only come from these servers.” Messages that are coming from servers other than those specified in the SPF record will be viewed as spam and ignored. Below is an example of an SPF record for an example domain:
IN TXT "v=spf1 ip4:192.0.2.12 ip4:192.0.2.130 -all"
This record tells us that the IPv4 addresses 192.0.2.1 and 192.0.2.129 are allowed to send email for the designated domain. With the use of “-all,” we stress that only mail that matches this pattern of IPv4 addresses is allowed.
IsoPropyl Alcohol (IPA) is recommended for cleaning PCAs such as motherboards. Mild detergent can be used for cleaning the outside cabinet or the keyboard.
When attending to the computer maintenance or repair (other than the monitor), ensure that you work in a static free environment. Always wear wrist strap. You should not wear clothes/shoes that produce static charges. You should not use an Electrostatic Discharge (ESD) wrist strap when working on an open Cathode Ray Tube (CRT) display. An ESD wrist strap grounds your body to protect components from an ESD shock. However, a CRT display is highly charged, so you do not want to be grounded when you work inside one. In fact, only specially trained personnel should ever open a CRT display.
DLL stands for Dynamic Link Library. DLL is a special form of application code loaded into memory by request. A DLL is not executable by itself. More than one application may use the functions offered by a DLL.
Boot Options: The Advanced Boot Options menu lets you start Windows in advanced troubleshooting modes. The options available are
1. Repair your computer
2. Safe mode
3. Safe mode with networking
4. Safe mode with command prompt
5. Enable boot logging
6. Enable low resolution video (640 x 480)
7. Last Known Good Configuration (advanced)
8. Directory services restore mode
9. Debugging mode
10. Disable automatic restart on system failure
11. Disable Driver Signature Enforcement
12. Start Windows normally
NTLDR (New Technology Loader) Missing error: If your Microsoft Windows 10-based computer does not start correctly or if it does not start at all, you can use the Windows Recovery Options to help you recover your system software. The causes for an error message like: 'NTLDR is Missing, Press any key to restart', may be due to any of the following reasons:
1. Computer is booting from a non-bootable source.
2. Computer hard disk drive is not properly setup in BIOS.
3. Corrupt NTLDR and/or NTDETECT.COM file.
4. Attempting to upgrade from a Windows 95, 98, or ME computer that is using FAT32.
5. Corrupt boot sector / master boot record.
6. Loose or Faulty IDE/EIDE hard disk drive cable.
1. Insert the Windows 7 installation disc or USB flash drive, or a system repair disc, and then shut down your computer.
2. Restart your computer using the computer's power button.
Automated System Recovery(ASR): ASR is a part of an overall plan for system recovery so that you are prepared if the system fails. ASR should be a last resort for system recovery. Use ASR only after you have exhausted other options. It is recommended that you use ASR only if all other options to repair the system (such as Last Known Good, and Safe Boot) have failed.
Steps to create Windows Automated System Recovery Disk on Windows 7
1. From the Start menu, select Control Panel.
2. Click Backup and Restore, and then on the left, choose Create a system repair disc.
3. Select a drive, and then click create.
MSCONFIG: Short for Microsoft System Configuration Utility is designed to help you troubleshoot problems with your computer, MSCONFIG can also be used to ensure that your computer boots faster. Every time you boot your computer a lot of "hidden" programs load in the background. Some of these hidden programs are essential, but most aren't. Turning off some of these hidden programs (or services) can significantly increase your computer's performance and reliability.
For example, you want to disable DLP program from your computer from startup. To do so, you access MSconfig (System Configuration utility), and then the Services and Startup tabs in order to disable the two components of DLP 2.0 (DLP short for Data Loss Prevention).
1. The Startup tab will allow you to disable the actual application stored in Program Files, stopping the application from starting up when the user logs in.
2. The Services tab will allow you to disable the underlying service so that fewer resources are used, and there is less chance of system issues.
3. The General tab gives you several different startup selections.
4. The Boot tab allows you to modify how the system boots.
5. The Tools tab enables you to launch various OS utilities directly from Msconfig.
Event Logs: Event Log Explorer helps you to quickly browse, find and report on problems, security warnings and all other events that are generated within Windows.
Available logs in Windows 7 are:
1. Application(program): Events are classified as error, warning, or information, depending on the severity of the event. An error is a significant problem, such as loss of data. A warning is an event that isn't necessarily significant, but might indicate a possible future problem. An information event describes the successful operation of a program, driver, or service.
2. Security:These events are called audits and are described as successful or failed depending on the event, such as whether a user trying to log on to Windows was successful.
3. Setup: Computers that are configured as domain controllers will have additional logs displayed here.
4. System: System events are logged by Windows and Windows system services, and are classified as error, warning, or information.
5. Forwarded Events: These events are forwarded to this log by other computers.
Some of the troubleshooting tools
Process Kill: If you prefer to kill processes using the Command Prompt, you can do it. You have to run the Command Prompt as Administrator. To do this just right click command prompt from "All Programs > Accessories > Command Prompt" then select "Run as Administrator" on the pop-up menu.
On the Command Prompt, perform the following.
1. Type "tasklist" and press enter. It will show you a list of all the running processes.
2. Now you can End any particular process by executing the "Task kill" command.
For Example: To kill Chrome just type “Task kill /IM chrome.exe /F”
Where:
/IM - Kill by Image Name
/F - Kill the process forcefully.
Of course, you can also do this using Task Manager without going to the command prompt.
1. The Windows 10 recovery environment (WinRE) is also known as System recovery options and recovery console.
2. Windows 10's Recovery Environment enables users to perform a variety of system and data recovery tasks on a system that won't boot normally, including:
Fixing boot-level startup problems (Startup Repair)
Returning your system to a previous configuration (System Restore)
Recovering your computer with a previously-created system image (System Image Recovery)
Checking for defective memory (Windows Memory Diagnostic)
Running command-prompt programs (Command Prompt)
3. Advanced Boot Options is the menu that can be accessed by holding down the Shift key on your keyboard and restart the PC. Windows will automatically start in advanced boot options after a short delay.

It is very important that you verify that the backup is working properly. It may so happen that you have several backup tapes, but none of them is good.
SFC: Sfc /scannow will inspect all of the important Windows files on your computer, including Windows DLL files. If System File Checker finds an issue with any of these protected files, it will replace it. You must be logged in as a user with administrator rights in order to run the sfc /scannow command.
Driver Verifier: Driver Verifier monitors Windows kernel-mode drivers and graphics drivers to detect illegal function calls or actions that might corrupt the system. Driver Verifier can subject Windows drivers to a variety of stresses and tests to find improper behavior. You can configure which tests to run, which allows you to put a driver through heavy stress loads or through more streamlined testing. You can also run Driver Verifier on multiple drivers simultaneously, or on one driver at a time. You can use this tool to troubleshoot driver issues. It is available in all versions of Windows starting with Windows 2000. Each version introduces new features and checks for finding bugs in Windows drivers. This section summarizes the changes and provides links to related documentation.
Caution:
1. Running Driver Verifier could cause the computer to crash.
2. You should only run Driver Verifier on computers that you are using for testing and debugging.
4. You must be in the Administrators group on the computer to use Driver Verifier.
5. Driver Verifier is not included in Windows 10 S, so we recommend testing driver
6. behavior on Windows 10 instead.
You can start the tool by going to Run > verifier.exe
1. You can start verification of any driver without rebooting, even if Driver Verifier is not already running.
2. You can start the verification of a driver that is already loaded.
3. You can activate or deactivate most Driver Verifier options without rebooting.
PC Security Issues with appropriate tools
Traditionally, antivirus software relies upon signatures to identify malware. This can be very effective, but cannot defend against malware unless samples have already been obtained, signatures generated and updates distributed to users. Because of this, signature-based approaches are not effective against zero-day viruses.
A zero-day (or zero-hour or day zero) attack or threat is an attack that exploits a previously unknown vulnerability in a computer application, meaning that the attack occurs on "day zero" of awareness of the vulnerability. This means that the developers have had zero days to address and patch the vulnerability.
It is possible that sensitive information is relayed to the hacker unless the infected system is disconnected from the network. It may also infect other systems by remote triggering.
System Restore automatically track changes to your computer and creates restore points before major changes are to occur. To create a restore point, System Restore takes a full snapshot of the registry and some dynamic system files. For example, restore points are created before new device drivers, automatic updates, unsigned drivers, and some applications are installed. To create a System Restore Point in Windows 10, use the sequence, Start | All Apps|Windows Accessories | System Tools, and then click System Restore. Alternatively, you may just type "restore" in the search box, and click on the "System Restore" option that appears above.

