Screen Locks: Apple and Android mobile devices include a requisite locking mechanism, which is off by default. The user can enable these locks. The following are types of locks that you can implement to secure your device.
Fingerprint lock: A fingerprint lock has a built-in fingerprint reader that is used to access the device. It is a biometric-type of lock that uses your fingerprint to unlock the device. This works by placing your finger on a touchpad sensor on the device.

Face lock: Face lock uses the built-in camera to identify the users face to allow access. There are a high number of false positives that makes the face lock less secure than the fingerprint lock. This means that presumably someone that looks like you could unlock your phone.
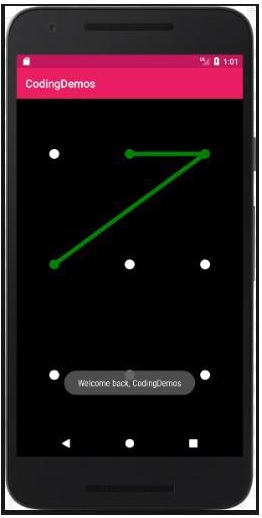
Swipe lock: Swipe lock has a predefined pattern that users outline with their finger to allow access. The swipe lock works by displaying nine dots in a matrix of 3x3. You then swipe with your finger with the registered pattern to unlock the phone. The swipe lock is the least secure of any locking methods. A grease trail from your fingers can allow someone to derive the swipe pattern.
Passcode lock: Passcode lock uses a personal identification number (PIN) to access the device. It is a 4-6 digit numeric passcode or a alphanumeric depending on the device. Passcode locks suffer from the same problems that password are prone to: People can shoulder surf or learn your passcode over time.
Remote wipes: In the event of a lost or stolen your mobile device the capability to remotely delete all of the data on the device is extremely important to the device security. In most cases the security measures given above will be sufficient to secure your data. When you are sure the device cannot be recovered or you think the security measures will not withstand a breach, you have no choice but to clear all personal data from the device. This operation will return the device to its factory settings. Remote wipe program may or may not have the capability to clear data from SD cards that may be installed on the device. Some apps are capable of this feature and if there is a risk you should select your remote software accordingly.
Locator applications: If you have misplaced a device, all mobile operating systems support a degree of interactive device location. The Android Device Manager for the Android OS uses Google Maps and the location information last reported by the device to provide the last known location. In some cases this may be sufficient to find the device by simply activating the ringer. This application allows you to Ring the device, lock it or remotely wipe your personal data returning the device to its out of the box configuration. However, note that either the remote wipe or the locator apps will not work if the service is powered off or has its SIM card removed.
Remote backup applications: Each mobile operating system supports backups to the cloud. This is in the form of iTunes and iCloud of Apple devices, OneDrive for Microsoft and Google Drive on Android. Access to these storage locations are controlled for the most part by email specific logins. For example you would create User@domain.com for a Microsoft account, User@gmail.com on Android and your personal apple ID to access Apple services like iTunes and iCloud Drive, other free backup and storage locations include Dropbox and others. You will find that all free backup services have either feature or size limitations or both. iCloud is geared toward storage, while iTunes handles backups and synchronization.
Failed login attempts restrictions: Primarily the mobile devices can be configured to lock after a specified number of login attempts. This is usually a temporary condition providing you with the time necessary to remember your password. In the conventional PC environment it is common to see login restrictions like the number of failed attempts that are allowed before the account locks. The number of attempts allowed can be reset, but it is important to know that on an iPhone for example, after an excessive number of attempts the device will permanently lock and erase all data. In most cases the access can be restored by using the primary account and password data. Providing, of course, that the device has not been erased.
Patching/OS updates: A patch modifies the existing software to add security features or operational improvements also known as bug fixes. Critical patches are known as hotfixes. A Service Pack refers to a group of patches and hot fixes compiled into a single download and install as a cumulative update. In the mobile environment the programming on the device is being constantly tested for vulnerabilities. As important as it is to keep your device virus and malware protection up to date, it is equally important to allow your mobile OS to patch and update its software. A widely used technique to trick you into installing malware employs a fake download site loaded with malware infected drivers.
Biometric authentication: One approach is biometric authentication, a system that relies on the unique biological characteristics (such as retina, voice, fingerprint, signature) of individuals to verify identity for secure access to electronic systems. The benefits of using biometrics for user authentication are evident. Whether it is a retina scan, a fingerprint or using your voice, the user always has their "password" with them and it is never forgotten. For the most part, it is easy to use because it is on someone’s person and all they need to do is "show up." If your employees already have devices equipped with the appropriate biometric readers, it may be an affordable approach. However, as with any technology, there are some downsides to using biometrics for authentication. One of those challenges is that you are introducing a high level of dependencies in your organization. Implementing biometric authentication can prove expensive and inconvenient, as initial provisioning of users requires a tamper-proof process to link identity and biometric data. Additionally, workers may no longer be able to login from devices other than their company-issued computer as their private tablet or PC may not have the necessary biometric scanner.
Full device encryption: Encryption is a highly effective security measure for files, folders even volumes. Encrypted content is digital junk without the decryption key. This enhanced security comes with a system performance penalty. The solution to this performance impact is whole device encryption which encrypts everything decreasing any internal operational performance lag.
Multifactor authentication: The combination of more than one authentication method is called multifactor authentication. Smartphones or other mobile devices can play an integral part in this process. Multifactor methods are frequently used by financial institutions to prevent unauthorized access and intrusion. Some multifactor authentication implementations use an email /password combination to initiate a callback or text back passphrase delivery. This will be in the form of a one-time passphrase (OTP) delivered to the mobile device then used as the second element of authentication. Also where the mobile device connectivity cannot be assured the multifactor method can have an email/password combined with facial recognition to provide the necessary security level.
Authenticator applications: An authenticator app works with mobile devices to generate security codes that can keep accounts secure by requiring 2 factor authentication. Once this is setup, your account will require a code from the app in addition to your account password. An account is usually added to the authenticator applications by entering a secret key or scanning a QR barcode, this creates the account in the authenticator applications.
Trusted sources vs. untrusted sources: Software drivers and other apps can easily be corrupted to allow malware to operate. You should study any system errors and verify the source of all errors and warnings. Once you are satisfied, always start with the manufacturer’s recommended website when updating any elements of your system. This is Google Play for Android and Apple’s App Store for iOS and the Microsoft Store for Windows based devices. Use the device settings where possible to block or restrict unknown or untrusted sites. It is necessary to examine the actual sources of everything you install on your machine. Given the possibility of misdirected web traffic look at the URLs carefully. It’s essential to understand the importance of using trusted sites to obtain your software. Also know the consequences of installing untrusted content up to and including identity theft and complete device failures.
Firewalls: The firewall system is set up to block any unauthorized access to the mobile communications system. On a mobile device some features of the firewall are configured during individual app installations. Each app requests specific permissions to install. Review these permissions for their relationship to the app operation and whether or not you wish to grant it. A mobile device firewall app will allow you to monitor both the inbound and outbound communications on your mobile device.
Policies and procedures: With this explosive growth of mobile devices in the workplace, there are many different policies and procedures that may be required for organization to minimize data loss.
BYOD vs. corporate owned: The term BYOD (Bring your Own Device) describes a corporate policy that allows an employee to use their own device in the corporate environment. This includes evaluation by the company IT department to be sure the device meets the corporate security requirements regarding software, patches, anti-malware, firewall, VPN, login requirements and encryption. Any software installation needed to meet the BYOD policy are referred to as on-boarding. Corporate owned devices are configured to meet these same requirements.
Profile security requirements: This policy will be clearly outlined and enforced. The policy will also include provisions for wiping the data from lost/stolen devices or employees that have been dismissed.

