Networking tools:
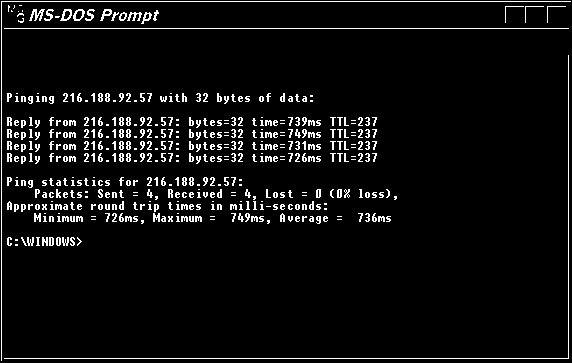
PING: Used to ping the remote system (or the local host) to see that the TCP/IP connection is through. The following fig shows output from ping command.
You can ping the loop back address at 127.0.0.1. A response ensures that the TCP/IP stack is installed properly on your computer.
List of ping command
1. Ping -r: this ping command option used to specify the number of hops between your computer and the target computer or device that you'd like to be recorded and displayed.
2. Ping -a: This ping command option will resolve, if possible, the hostname of an IP address target.
3. Ping -v: This option allows you to set a Type of Service (TOS) value. Beginning in Windows 7, this option no longer functions but still exists for compatibility reasons.
4. Ping -n: This option sets the number of ICMP Echo Request messages to send. If you execute the ping command without this option, four requests will be sent.
5. Ping -t: this option will ping the target until you force it to stop using Ctrl-C.

The pathping command is a route tracing tool that combines features of the ping and tracert commands with additional information that neither of those tools provides.
NBTSTAT: This utility displays current NetBIOS over TCP/IP connections, and display NetBIOS name cache. It Displays protocol statistics and current TCP/IP connections since the server was last booted. NETSTAT is used to review all inbound / outbound connection to a server.
NSLOOKUP: This utility enables users to interact with a DNS server and display resource records.
ROUTE: Used to display and edit static routing tables.
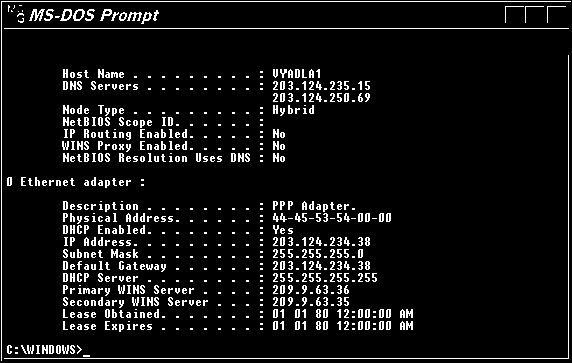
PCONFIG: Internet Protocol Configuration in Microsoft Windows is a console application that displays all current TCP/IP network configuration values and can modify Dynamic Host Configuration Protocol DHCP and Domain Name System DNS settings. The following fig shows the output of ipconfig command.

ipconfig /all: Displays the full TCP/IP configuration for all adapters. Without this parameter,
ipconfig displays only IPv6/IPV4 addresses, subnet mask, and default gateway values for each adapter. The command IPCONFIG/ALL shows additional parameters such as host name, DNS servers etc. compared to IPCONFIG command which doesn't show these details
ifconfig (short for interface configuration) is a system administration utility in Unix-like operating systems to configure, control, and query TCP/IP network interface parameters from a command line interface (CLI) or in system configuration scripts. Ifconfig is used to configure and display network interfaces. If no arguments are given, ifconfig displays the status of the currently active interfaces. If a single interface argument is given, it displays the status of the given interface only. If a single -a argument is given, it displays the status of all interfaces, even those that are down.
netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface (network interface controller or software-defined network interface) and network protocol statistics. It is available on Unix-like operating systems including OS X, and Linux, and is available on Windows NT-based operating systems including Windows 7/8, and Windows 10.
Netstat provides statistics for the following:
Examples
To display both the Ethernet statistics and the statistics for all protocols, type the following command:netstat -e -s
To display the statistics for only the TCP and UDP protocols, type the following command:netstat -s -p tcp udp
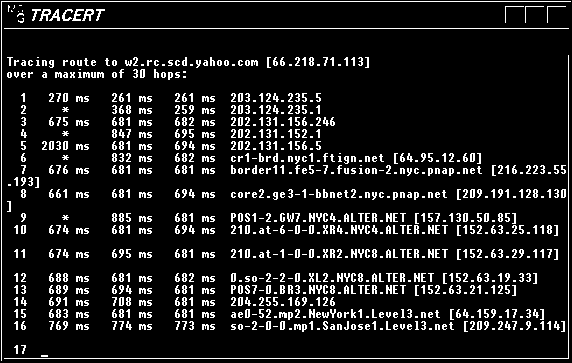
TRACERT: Used to determine which route a packet takes to reach its destination from source. The tracert utility traces the path to the destination. It is accomplished by controlling the TTL (Time To Live) of the packets in the increments of 1 (one). When the TTL reaches 0, the router sends back an error message saying that the TTL has elapsed. This information is used to find the intermediate devices over the path to destination. Note that some routers may be programmed not to respond to TTL 0 packets. In such event, you may not receive any response.

Tracert and Ping use ICMP as their base protocol. ICMP messages are carried in IP datagrams. The command tracert/traceroute displays the time taken while a packet reach the destination. You will be able to see the time taken by each hop, and identify the faulty link.
The following fig shows tracert command output
Given below are some of the precautions that may be required to secure the local network resources:
1. Rename default accounts so that blind attacks will not succeed
2. Use strong passwords and change passwords periodically
3. Secure the server rooms with lock and key
4. Use strong encryption for user names and passwords
Note that disabling local admin access is not an option because your manager wants to administer the servers locally. Anti virus software will not protect a server from un-authorized login.