RETIRED! Exam
Network Address Translation (NAT) you choose to implement depends on what your goals are for NAT and your public address management. NAT methods include
Static NAT: Puts a permanent mapping between an internal private address and a public address. In this scenario, 192.168.8.50 will always map out to 192.0.2.75. This type of NAT may be used for allowing traffic into a mail server or web server that is internal to your network.
Dynamic NAT: Puts a dynamic mapping between an internal private address and a public address. This also creates a one-to-one relationship on a first-come-first-served basis. The public address that is used by private devices can change over time and cannot be trusted.
Overloading: This is also known as Port Address Translation (PAT). In this case, multiple internal devices are able to share one public address, as mappings are placed into the mappings table based on the source and destination ports that are used. As long as ports are available to be remapped, then any number of devices can share a very small pool of public addresses or just one public address.
Overlapping: NAT can be used when public or registered addresses are used inside your network. In this case, you may use a public address block on multiple internal networks. NAT allows you to translate those "internal" addresses to other publicly accessible addresses when you connect to the "public" side of the router.
The following are true about NAT
1. NAT allows several hosts be connected to Internet by using fewer globally unique IP addresses. This in turn results in conserving the scarce public IP addresses. The terms public / global is used in the sense that the IP addresses are globally unique and officially registered.
2. NAT supports load sharing on inside machines. The inside machines are accessed in a round robin fashion, thus sharing load.
3. NAT offers some degree of security since IP addresses are not easily traceable. This is because, the actual host IP that is accessing the Internet is translated into outside IP address and vice versa. Thus, NAT offers protection against hacking.
4. One disadvantage of NAT is that it increases delay. This is obvious since address translation is involved.
5. Another disadvantage of NAT is that, when an application uses physical IP address, it may not function properly. This is because the physical IP address is changed by NAT.
Important Network Address Translation (NAT) terms of inside local, inside global, outside local, and outside global are explained below:
1. Inside local : A private IP address assigned to a host on the inside network.
2. Inside global : A public IP address that represents one or more inside local IP addresses to the outside world.
3. Outside local : The IP address of an outside host as it appears to the inside network. Not necessarily a legitimate address, it is allocated from an address space routable on the inside.
4. Outside global : The IP address assigned to a host on the outside network. The address is allocated from a globally routable address or network space.
The following two statements are true about dynamic NAT translations:
1. The inside IP addresses eligible for address translation are defined in a standard IP access-list.
2. Only packets moving between inside and outside networks will get translated. This is true even for static NAT. If a packet is destined for another host, but does not require to cross the NAT boundary, the packet source/destination addresses are not translated. This is understandable, since the packet is not crossing the inside network boundary.
Enable dynamic NAT on an interface include the following:
1. Defining a standard IP access-list using the command:
access-list <access-list-number> {permit | deny} <local-ip-address>
2. Defining an IP NAT pool for the inside network using the command:
ip nat pool <pool-name> <start-ip> <end-ip> {netmask <net-mask> | prefix-length <prefix-length>} [type-rotary]
Note that type-rotary is optional command. It indicates that the IP address range in the address pool identifies hosts among which TCP load is distributed.
3. Mapping the access-list to the IP NAT pool by using the command:
ip nat inside source list <access-list-number> pool <pool-name>
4. Enabling NAT on at least one inside and one outside interface using the command:
ip nat {inside | outside}
The following command configures a static NAT translation by mapping inside local address to the inside global address.
ip nat inside source static 192.168.0.100 88.248.153.137
Here, 192.168.0.100 is the inside local address, and 88.248.153.137 is the inside global address. A packet's source address 192.168.0.100 is changed to 88.248.153.137 by the NAT device.
When you are configuring NAT, NAT should be enabled on at least one inside and one outside interface.
The correct syntax for enabling dynamic NAT to translate many inside hosts to an inside global IP address is:
ip nat inside source list <access-list-number> pool <pool-name> overload
where <access-list-number > is the standard access list number, and <pool-name > is the pool name.
Note that the option 'overload' specifies many to one relationship.
This configuration is typically used when many hosts with private IP addresses need to access Internet through a specified globally unique IP address.
Example: Please refer to the figure. Hosts on the network 192.168.1.0/24 are configured to access the Internet through router configured for NAT. Assuming that the NAT is working properly, which of the following could be the source address of packets leaving port s0 of the NAT router?
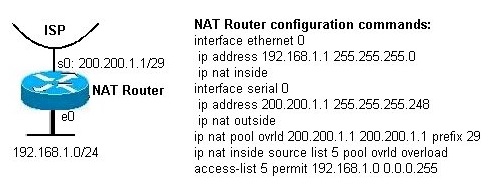
Solution: Note that the packets leaving port S0 on the NAT router should have global IP addresses. The source IP address should be within the pool allocated. In this case, only one IP address is allocated with "overload" command. Hence, the public IP 200.200.1.1 will be used as the source IP address for a packet leaving the NAT router.
NAT traversal (or network address translation traversal): is a computer networking methodology that ensures IP connectivity across gateways that implement network address translation (NAT). NAT breaks the principle of end-to-end connectivity originally envisioned in the design of the Internet.
Following are true about NAT Traversal:
Hairpinning behavior: Hairpin is a behavior where a NAT device forwards packets from a host in internal network (lets call it host A) back to some other host (host B) in the same internal network, when it detects that the (public IP address) destination of the packet is actually a mapped IP address that was created for the internal host (host B). This is a desirable behavior of a NAT, but unfortunately not all NAT devices support this.
Lacking this behavior, two (internal) hosts behind the same NAT will not be able to communicate with each other if they exchange their public addresses (resolved by STUN above) to each other.
Traditional NAT handles only outbound transactions; clients on the local network initiate requests and servers on the Internet send back responses. However, sometimes, we may want to have a device on the outside network initiate a transaction with one on the inside. To permit this, we need a Bidirectional NAT, Two-Way NAT, or Inbound NAT. All of these convey the concept that the transactions initiated from the outside network.
However, the internal network consists of private addresses that are hidden from the Internet.
There are two methods to resolve the hidden address problem.

