Extensible Authentication Protocol (EAP): A standardized authentication framework defined by RFC 4187 that provides encapsulated transport for authentication parameters. EAP authentication types provide a potentially better means of securing the WLAN connection. Some of the most commonly deployed EAP authentication types include EAP-MD-5, EAP-TLS, EAP-PEAP, EAP-TTLS, EAP-Fast, and Cisco LEAP. EAP-TTLS and PEAP requires server-side certificate where as EAP-TLS requires both client and server side certificates.
Extensible Authentication Protocol (EAP): A standardized authentication framework defined by RFC 4187 that provides encapsulated transport for authentication parameters. There are many different EAP authentication methods available, most of them based on Transport Layer Security (TLS).
Following is a description of each of the EAP authentication methods:
EAP-MD5: Uses the MD5 message-digest algorithm to hide the credentials in a hash. The hash is sent to the authentication server,where it is compared to a local hash to validate the accuracy of the credentials. EAP-MD5 does not have a mechanism for mutual authentication; in other words, the authentication server validates the supplicant, but the supplicant does not validate the authentication server to see if it is trustworthy. This lack of mutual authentication makes it a poor choice as an authentication method.
EAP-TLS: Uses the TLS Public Key Infrastructure (PKI) certificate authentication mechanism to provide mutual authentication of supplicant to authentication server and authentication server to supplicant. With EAP-TLS, both the supplicant and the authentication server must be assigned a digital certificate signed by a certificate authority (CA) that they both trust. Because the supplicant also requires a certificate, this is the most secure authentication method; however, it is also the most difficult to deploy due to the administrative burden of having to install a certificate on the supplicant side.
PEAP(Protected Extensible Authentication Protocol): In PEAP, only the authentication server requires a certificate, which reduces the administrative burden of implementing EAP. PEAP forms an encrypted TLS tunnel between the supplicant and the authentication server.
EAP-TLS: This is the most secure EAP authentication since it is essentially a TLS tunnel within another TLS tunnel. It is rarely used due to its deployment complexity because it requires certificates to be installed on the supplicants.
EAP-FAST: EAP-FAST, which is similar to PEAP, was developed by Cisco Systems as an alternative to PEAP to allow for faster re-authentications and support for faster wireless roaming. Just like PEAP, EAP-FAST forms a TLS outer tunnel and then transmits the client authentication credentials within that outer TLS tunnel. EAP-FAST includes the option of EAP chaining, which supports machine and user authentication inside a single outer TLS tunnel.
EAP-TTLS: EAP-TTLS is similar in functionality to PEAP but is not as widely supported as PEAP. One major difference between them is that PEAP only supports EAP inner authentication methods, while EAP-TTLS can support additional inner methods such as legacy Password Authentication Protocol (PAP), Challenge Handshake Authentication Protocol (CHAP), and Microsoft Challenge Handshake Authentication Protocol (MS-CHAP).
Local EAP is an authentication method that allows users and wireless clients to be authenticated locally on the controller. It is designed for use in remote offices that want to maintain connectivity to wireless clients when the backend system becomes disrupted or the external authentication server goes down. When you enable local EAP, the controller serves as the authentication server and the local user database, so it removes dependence on an external authentication server. Local EAP retrieves user credentials from the local user database or the LDAP backend database to authenticate users. Local EAP supports LEAP, EAP-FAST, EAP-TLS, PEAP authentication between the controller and wireless clients. Local EAP can use an LDAP server as its backend database to retrieve user credentials.
Web Authentication or Web Auth is a layer 3 security method that allow client to pass DHCP & DNS traffic only untill they have passed some form of authentication. This is greatly used in wireless guest access service where no client side configuration required.
WLC has four authentication policies.
1. Authentication
2. Passthrough
3. Conditional Web Redirect
4. Splash Page Web Redirect
Below shows the authentication policies on layer 3 security tab for a given WLAN of WLC with 7.0.116.0 code.
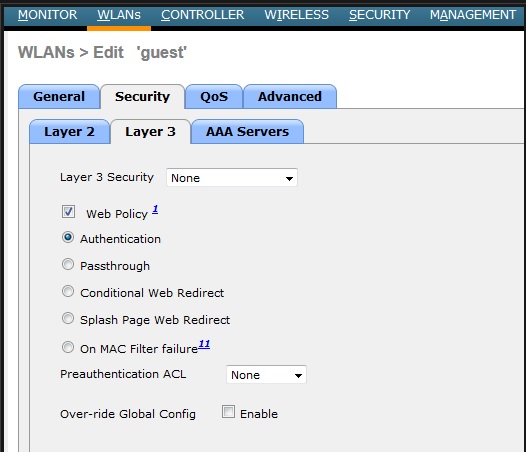
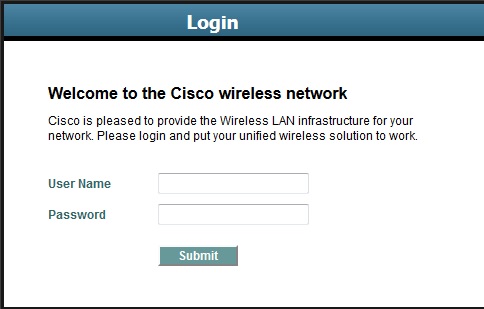
When you enable Authentication option (as shown in the above screen capture), a guest client has to enter a username & password to gain access to the guest network. Once user get an IP & try to access an URL it authentication screen appear like this.
Phase-shift keying (PSK) is a digital modulation process which conveys data by changing (modulating) the phase of a constant frequency reference signal (the carrier wave). A symmetric algorithm is one which uses the same key for encryption and decryption. Examples of symmetric algorithm are DES, 3DES, AES, and IDEA. An asymmetric algorithm is one which uses different keys for encryption and decryption. Examples of asymmetric algorithm are RSA, and Diffie-Hellman.
According to Cisco, security solutions for an organization may be broadly divided into three categories. These are:
A. Physical security: The following form physical security
a. Security cameras, and other monitoring devices
b. Security personnel
c. Climatic controls for proper temperature, humidity, etc.
d. Physical barriers
B. Administrative security: the following form administrative security
a. Maintaining log books
b. Screening employees, and security personnel
c. Maintaining security policies
d. Security awareness programs, etc.
C. Logical security
a. Authentication systems
b. Firewalls
c. Encryption schemes, etc.
Confidentiality, integrity and availability, also known as the CIA triad, is a model designed to guide policies for information security within an organization. The elements of the triad are considered the three most crucial components of security. Confidentiality is a set of rules that limits access to information, integrity is the assurance that the information is trustworthy and accurate, and availability is a guarantee of reliable access to the information by authorized people.
To secure wireless connections on a WLAN, you can use one of the Wi-Fi Protected Access (WPA) versions -WPA (also known as WPA1), WPA2, or WPA3. All three WPA versions support two client authentication modes, Pre-Shared Key (PSK) or 802.1x, depending on the scale of the deployment. These are also known as personal mode and enterprise mode, respectively. With personal mode, a key string must be shared or configured on every client and AP before the clients can connect to the wireless network. The pre-shared key is normally kept confidential so that unauthorized users have no knowledge of it. The key string is never sent over the air. Instead, clients and APs work through a four-way handshake procedure that uses the pre-shared key string to construct and exchange encryption key material that can be openly exchanged.
Extensible Authentication Protocol (EAP):EAP can support multiple authentication mechanisms, such as token cards, smart cards, certificates, one-time passwords, and public key encryption authentication. It can integrate with the IEEE 802.1x port-based access control standard. When 802.1x is enabled, it limits access to a network medium until a client authenticates. This means that a wireless client might be able to associate with an AP but will not be able to pass data to any other part of the network until it successfully authenticates.
Open authentication: It is one of the two authentication methods from the first 802.11 standard. As the name implies, open authentication offers open authentication to a wireless network. The wireless client sends an authentication request to the AP, which the AP accepts without question. You dont need a pre-shared key or credentials. After authentication, the wireless client associates with the AP.
Wired Equivalent Privacy (WEP): WEP is a security algorithm and the second authentication option that the first 802.11 standard supports. The idea behind WEP is to make a wireless network as secure as a wired link. WEP has become obsolete and rarely used.
WPA: WPA stands for Wi-Fi Protected Access. There are two versions of WPA: WPA and WPA2. WPA is a standards-based security solution from the Wi-Fi Alliance that addresses the vulnerabilities in native WLANs and provides enhanced protection from targeted attacks.
Endpoint security is an approach to secure computer networks and all client devices remotely bridged to the network. Endpoints are devices such as laptops, desktops, mobile phones, etc., that are connected across networks. These devices serve as entry points for cybercriminals looking to gain unauthorized access to sensitive assets and information.
An endpoint is a spot where two devices interact in a network. It includes a wide array of devices that employ remote connectivity. Some examples of endpoints that require security are:
Desktops
Laptops
Smartphones
IoT devices
Workstations
Servers
Tablets
Endpoint security helps you protect your assets from hackers in the following ways:
1. It monitors an application's activity for any threats. It’s connected to the cloud, where its directories update dynamically to save your assets from multivector threats and zero-day attacks.
2. It secures sensitive data exchanged between partners and vendors while maintaining confidentiality.
3. It prevents third-party applications from establishing a connection with your devices and includes various security procedures to ensure comprehensive security.
4. It ensures network security by monitoring and alerting whenever the endpoint security tool spots an anomaly.
5. It protects individual devices and enterprise networks from threats and allows better flexibility and functionality in the company.
NGFW: A next-generation firewall (NGFW) is a security appliance that processes network traffic and applies rules to block potentially dangerous traffic. NGFWs evolve and expand upon the capabilities of traditional firewalls. They do all that firewalls do, but more powerfully and with additional features.
Benefits of Next Generation Firewall
The differentiating features of next generation firewalls create unique benefits for the companies using them. NGFWs are able to block malware from entering a network, something that traditional firewalls would never be able to achieve. They are better equipped to address Advanced Persistent Threats (APTs). NGFWs can be a low-cost option for companies looking to improve their basic security because they can incorporate the work of antiviruses, firewalls, and other security applications into one solution. The features of this include application awareness, inspection services, as well as a protection system and awareness tool that benefit
TrustSec is a next-generation access control enforcement solution developed by Cisco, to address the growing operational challenges related to maintaining firewall rules and ACLs by using Security Group Tag (SGT) tags. TrustSec uses SGT tags to perform ingress tagging and egress filtering to enforce access control policy.
TrustSec configuration occurs in three phases:
Ingress classification : Ingress classification is the process of assigning SGT tags to users, endpoints, or other resources as they ingress the TrustSec network, and it can happen in one of two ways: Dynamic assignment and Static assignment.
Propagation : Propagation is the process of communicating the mappings to the TrustSec network devices that will enforce policy based on SGT tags.
Egress enforcement : After the SGT tags have been assigned (classification) and are being transmitted across the network (propagation), policies can be enforced at the egress point of the TrustSec network.
The syntax for configuring a switch port to use 802.1x is:
Switch(config-if)# dot1x port-control [force-authorized | force-un-autorized | auto ]
Ports can be in one of three authorization modes. The first mode, force-authorized, and default mode. In first mode, a port is always authorized. Force-authorized mode is used when you do not want to run 802.1X on a particular port. This is typically the case when connecting to another switch, or a client PC that do not support 802.1X. The next mode, auto, is the normal 802.1X mode. A port in auto mode will not become authorized unless it receives a positive response from the authentication server. The final mode, force-unauthorized, prevents a port from becoming authorized even if the user has the appropriate credentials. This mode essentially disables the port from use by any user or device.
Web authentication (WebAuth) is Layer 3 security. It allows for user-friendly security that works on any station that runs a browser. It can also be combined with any pre-shared key (PSK) security (Layer 2 security policy). Web Authentication (WebAuth) presents the end user with content to read and interact with before granting access to the network. For example, it can present an Acceptable Use Policy (AUP) that the user must accept before accessing the network. It can also prompt for user credentials, display information about the enterprise, and so on. Naturally, the user must open a web browser to see the WebAuth content. WebAuth can be used as an additional layer in concert with Open Authentication, PSK-based authentication, and EAP based authentication. Web Authentication can be handled locally on the WLC for smaller environments through Local Web Authentication
(LWA). You can configure LWA in the following modes:
LWA with an internal database on the WLC
LWA with an external database on a RADIUS or LDAP server
LWA with an external redirect after authentication
LWA with an external splash page redirect, using an internal database on the WLC
LWA with pass through, requiring user acknowledgment

