VPN: Short for Virtual Private Network is private network formed using public Internet. It is formed between two hosts using tunneling protocols such as PPTP, L2TP, etc. Using VPN, you can connect two LANs in geographically distant locations together, as if they were located in the same building. The cost of connecting these LANs together is small since public Internet is used for providing the WAN link. A VPN provides a mechanism to access corporate networks safely using Internet. VPN uses encryption to ensure only authorized user can access the corporate resources. A secure tunnel is created through the public network through which the packets are transported between the remote computer and the corporate network. VPN are used for accessing a corporate network securely from remote locations using public Internet.
The host-to-host configuration provides the highest security for the data. However, a Gate-to-Gateway VPN is transparent to the end users.
The VPN can be implemented in any of the following combinations:
1. Gateway-to-gateway VPN
2. Gateway-to-host VPN
3. Host-to-gateway VPN
4. Host-to-host VPN

The host-to-host configuration provides the highest security for the data. However, a Gate-to-Gateway VPN is transparent to the end users.
There are two widely known protocols that can be implemented for enabling VPN communications:
1. PPTP
2. L2TP
PPTP stands for Point to Point Tunneling Protocol. It is a PPTP is pioneered by Microsoft and others is a widely used protocol.
L2TP stands for Layer Two (2) Tunneling Protocol. L2TP merges the best features of PPTP and L2F (from Cisco Systems).
PPTP and L2TP protocols together with PPP protocol enable ISPs to operate Virtual Private Networks (VPNs).
Ipsec: The two primary security services that are provided by IPSec are:
1. Authentication Header (AH), and
2. Encapsulating Security Payload(ESP)
AH: Authentication Header provides the authentication of the sender, and ESP provides encryption of the payload.
Hub: A hub is basically a multi-port repeater. When it receives a packet, it repeats that packet out each port. This means that all computers that are connected to the hub receive the packet whether it is intended for them or not. It's then up to the computer to ignore the packet if it's not addressed to it. This might not seem like a big deal, but imagine transferring a 50 MB file across a hub. Every computer connected to the hub gets sent that entire file (in essence) and has to ignore it.
HSM:A hardware security module (HSM) is a hardware encryption device that's connected to a server, typically using PCI, SCSI, serial, or USB interfaces and managed separately from the operating system. These modules provide a secure hardware store for CA keys, as well as a dedicated cryptographic processor to accelerate signing and encrypting operations.
DMZ:Demilitarized zone (DMZ) A network segment that exists in a semi-protected zone between the Internet and the inner, secure trusted network.
Jump Server: A jump host (also known as a jump server) is an intermediary host or an SSH gateway to a remote network, through which a connection can be made to another host in a dissimilar security zone, for example a demilitarized zone (DMZ). It bridges two dissimilar security zones and offers controlled access between them.
HTML5: HTML5 is the current version of the HTML protocol standard, and this version was developed to handle the modern web content of audio and video as well as to enhance the ability of a browser to function without add-ins such as Flash, Java, and browser helper objects for common functions.
Bridge: A bridge is a kind of repeater, but it has some intelligence. It learns the layer 2 (MAC) addresses of devices connected to it. This means that the bridge is smart enough to know when to forward packets across to the segments that it connects. Bridges can be used to reduce the size of a collision domain or to connect networks of differing media/topologies, such as connecting an Ethernet network to a Token Ring network.
Switch: A switch is essentially a multi-port bridge. The switch learns the MAC addresses of each computer connected to each of its ports. So, when a switch receives a packet, it only forwards the packet out the port that is connected to the destination MAC address. Remember that a hub sends the packet out every port.
Flood guard: Flood guard is a defence mechanism against flooding type of attacks such as distributed Denial of Service (DDoS) attacks. Floodguards are used to prevent massive attacks against a public or private network.
Router: A router works at the logical layer of the IP stack. It is basically required to route packets from one network (or subnet) to another network (or subnet). In the given question, all the computers are within the same subnet and a router is inappropriate.
Gateway: A gateway works at the top layers of the TCP/IP stack. For example, a Gateway may be used to facilitate communication between a Unix mail server and a Windows mail server.
Firewall:
NAT: NAT short for Network Address Translation device changes the source IP address of a packet passing through it. Because of this, the destination host would not be able to receive the packets. The NAT devices at either side need to be configured so that it allows VPN packets through it. It is primarily used to hide internal network from external network, such as the Internet. A NAT basically translates the internal IP addresses to external IP addresses and vice-versa. This functionality assures that external users do not see the internal IP addresses, and hence the hosts.
ACL(Access Control List): An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject, an operator, and an object. For instance, if a file has an ACL that contains (Alex, delete, file-name), this would give Alex permission to delete the file. ACLs are basically a set of commands, grouped together by a number or name that is used to filter traffic entering or leaving an interface. ACL statements are processed top-down until a match is found, and then no more statements in the list are processed. If no match is found in the ACL, the packet is dropped due to implicit deny. That is, you down type specifically to drop the traffic, but it is understood by the ACL to drop all traffic that does not match atleast one of the statements.
NIDS: As opposed to Network Intrusion Detection Systems (NIDS), Network Intrusion Prevention Systems (NIPS) focus on prevention. Arguably, NIPS is a subset of NIDS. Honeyspot is an example of NIPS
Vampire tape: A vampire tap is a type of connection that hooks directly into a coax by piercing the outer sheath and making contact with the center conductor. A vampire tap is widely used in 10Base5 networks. The mechanism allows an attacker to monitor network traffic without being detected.
Network Access Control (NAC): NAC controls access to a network with policies, including pre-admission checks and security policy checks and post-admission controls as and when a user or a device connects to a network and determines what they can do. Other schemes such as NAT, private addressing, and subnetting are only security mechanisms that take care of only one aspect of network security, and not policy based as in case of NAC.
Data loss prevention (DLP): DLP may used for making sure that end users do not send sensitive or critical information outside the corporate network. The term is also used to describe software products that help a network administrator control what data end users can transfer. DLP solution can be used to filter documents sent to a printer based on the content, thus disabling any sensitive data from being transmitted to the printer.
USB Blocking: Microsoft Windows 7 comes with bit locker technology to encrypt files. You can use the same to encrypt USB drive. Note that the motherboard also should support encryption for bit-locker technology to work. If you use file-level encryption, you need to encrypt the required file separately. That may again pose problem as you may forget to encrypt or forget the key used for file-level encryption. Further, some encryption programs does not support file-level encryption.
MAC Filtering: MAC filtering is a security access control method in which MAC address is used to determine access to the network. With MAC Filtering each host is identified by its MAC address and allowed (or denied) access based on that
SSL decryptor: Another layer of security can be added to the network with an SSL decryptor . These gateways decrypt encrypted traffic (SSL or TLS), inspect it, and then re-encrypt it before sending it on to its destination. It is a processor-intensive process, but the advantage it offers is in the inspection step-making sure that you are not forwarding problems that did not get caught simply because the data was encrypted.
Port spanning/port mirroring
Access Point (TAP): TAP is a passive signal-copying mechanism installed between two points on the network. The TAP can copy all packets it receives, rebuilding a copy of all messages. TAPs provide the one distinct advantage of not being overwhelmed by traffic levels, at least not in the process of data collection. Port taps, when placed between sending and receiving devices,can be used to carry out man-in-the-middle attacks. Thus, when placed by an unauthorized party, they can be a security risk.
An aggregator switches is a device that takes multiple inputs and combines them to a single output.
Port Spanning/Port Mirroring: Most enterprise switches have the ability to copy the activity of one or more ports through a Switch Port Analyzer (SPAN) port, also known as a port mirror. This traffic can then be sent to a device for analysis. Port mirrors can have issues when traffic levels get heavy, as the aggregate SPAN traffic can exceed the throughput of the device.
Mitigation techniques
Runbooks: Operations runbooks, often simply called runbooks, are a set of standardized documents, references, and procedures used to describe common IT tasks. Runbooks are created for the purpose of walking someone through the steps necessary for accomplishing a specific task or troubleshooting a particular issue
Playbooks: A playbook is a set of approved steps and actions required to successfully respond to a specific incident or threat. Playbooks are commonly instantiated as itemized checklists, with all pertinent data prefilled in systems, team members, actions, and so on.
Firewall rules: Firewall rules state whether the firewall should allow particular traffic to pass through or block it. The structure of a firewall rule can range from simple to very complex,depending on the type of firewall and the type of traffic.
Mobile Device Management (MDM): MDM is the term for a collective set of commonly employed protection elements associated with mobile devices.
Quarantine: In the case of a suspicious file, file change,or configuration change, there is a chance of error in the decision, and having a virtual "undo" capability may be desired. This is where the concept of quarantine enters the equation. Quarantining an item is to render it disabled but not permanently removed from the system.
Access point configuration
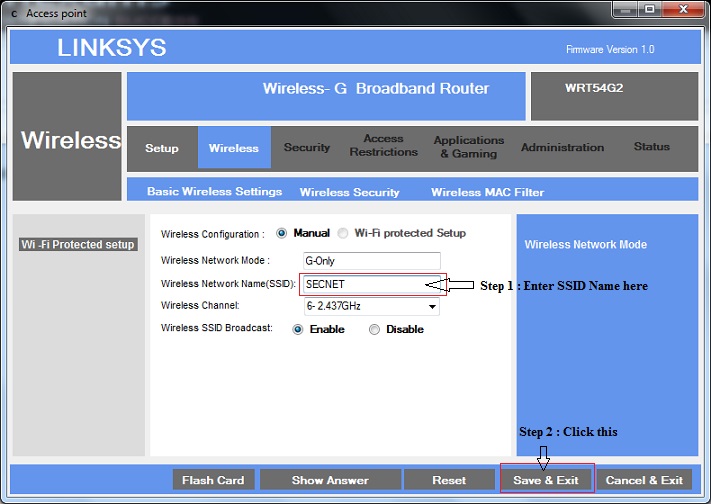
Example 1: Set SSID on the generic WAP router to SECNET.
Configuration steps:
Network Name (SSID) is basically the device's wireless network name and is one way of securing your wireless network. The SSID is shared by all devices in your wireless network and therefore, has to be unique since this will identify your wireless network from the rest.
To change the wireless network name of your router, follow the steps below.
Note: SSIDs are case sensitive and can contain up to 32 alphanumeric characters. Do not include spaces in your SSIDs.
1. In Access point window click "Wireless" tab

2. In that look for "Wireless Network Name" (SSID), and enter the SSID name "SECNET" in the box provided. Click on "Save & Exit" button.
Note: The exercise is typical for a particular brand of home router and may differ slightly from device to device. When you are configuring any other brand/make routers, please read the manufacturer's documentation provided along with the device.
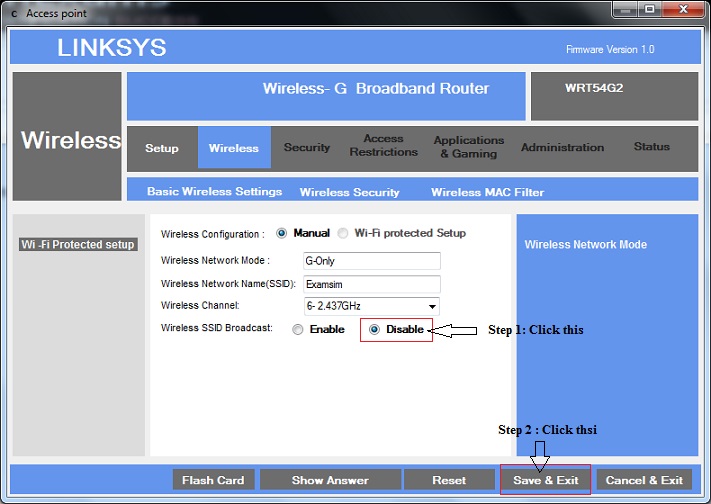
Example 2: Using the simulator, perform the task of disabling SSID broadcast.
A Service Set Identifier (SSID) is the wireless network name broadcast by the wireless device such as a wireless router. When another wireless device searches the area for wireless networks it will detect the SSID to be able to associate with the router. SSID Broadcast is enabled by default however; you may also choose to disable it.
Disabling the SSID Broadcast is one way of securing your wireless network. This procedure will prevent other users from detecting your SSID or your wireless network name when they attempt to view the available wireless networks in your area.
To disable the SSID Broadcast of your Linksys router, follow these steps:
1. In Access point window click "Wireless" tab

2. Click "Disable" radio button against "Wireless SSID Broadcast" and click "Save & Exit" button.